
SMALS STANDARDS
GDPR, de implicaties op een project en de bijhorende project deliverables worden toegelicht.- Leraar: Katleen Rolies

SMALS STANDARDS
Een initiatie rond information security@Smals.
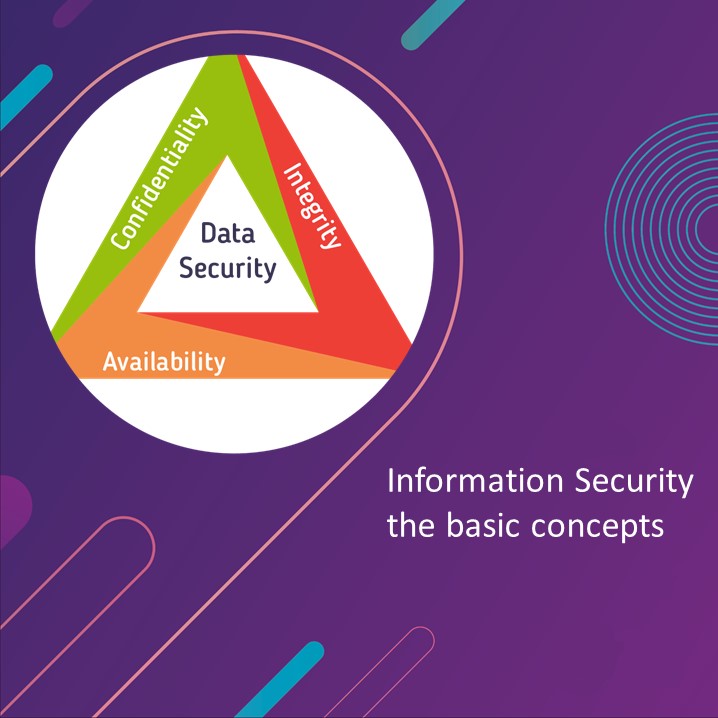
Je maakt kennis met de basisconcepten van Security, met name CIA (Confidentiality, Integrety, Availability) en beheer van privacy gegevens, worden je geïntroduceerd.
De verschillende rollen, verantwoordelijkheden, actoren en data protection worden uiteengezet.
Je maakt kennis met de teams Information Security, Entreprisk Risk Mgt en Application Security.
- Leraar: Katleen Rolies
SMALS STANDARDS
De basisconcepten data classification, CIA (Confidentiality, Integrety, Availability) worden uitgebreid toegelicht. Intrusion test, beter gekend als Pen Test & Vulnerabilities komen aan bod. Ook velden Security in project documenten worden besproken.
- Leraar: Katleen Rolies

Deze infosessie gaat over het thema ‘privacy & security aspecten van informatie systemen’. Tijdens deze sessies hebben we het specifiek over de ‘data protection impact analysis’ (DPIA), de gegevens-beschermings-effect-beoordeling.
- Leraar: Luc Herdewijn
- Leraar: Fabrice Provenaz
Learn how to protect information in your Microsoft 365 deployment. This course focuses on data lifecycle management and information protection and compliance within your organization. The course covers implementation of data loss prevention policies, sensitive information types, sensitivity labels, data retention policies, Microsoft Purview Message Encryption, audit, eDiscovery, and insider risk among other related topics. The course helps learners prepare for the Microsoft Information Protection Administrator exam (SC-400).
The information protection administrator translates an organization’s risk and compliance requirements into technical implementation. They are responsible for implementing and managing solutions for content classification, data loss prevention (DLP), information protection, data lifecycle management, records management, privacy, risk, and compliance. They also work with other roles that are responsible for governance, data, and security to evaluate and develop policies to address an organization's risk reduction and compliance goals. This role assists workload administrators, business application owners, human resources departments, and legal stakeholders to implement technology solutions that support the necessary policies and controls.

● Understand what incident response is
● Will have a list of incident response tools and resources
● Will have a list of templates to use
● Will have a list of incident response playbooks
Aanvraag indienen

● Define cryptography and the key role it plays in protecting our digital data
● Find out how Web sites use certificates to make sure our usernames, passwords, credit card numbers, and other personal data stay secure
● Understand ciphers, binary, hashing, symmetric and asymmetric cryptosystems, digital signatures and certificates, and public key infrastructure
● Learn how hashing helps us to be certain the data we receive or download is legitimate
● Prepare for the CompTIA Security+ exam by better understanding cryptography and PKI, one of the six exam domains
Aanvraag indienen

Duurtijd van de opleiding: 1,91u.
This course follows a proven methodology for conducting thorough and effective technical security audits and assessments based on guidelines from NIST. Learn how to develop the testing methodology essential for technical security reviews. Discover how to identify and analyze targets, use key technical testing tools, identify and mitigate findings, and more. Performing technical information security audits and assessments is essential to protecting information assets. By the end of this course, you'll know how to determine if your network is secure.
Topics include:
- Cite the three phases of external security assessments.
- Explain the reasons for conducting a log review.
- Explain what network sniffing is and why it’s used.
- Describe when to use a file integrity checking tool.
- Differentiate between active network discovery and passive network discovery.
- Explain how to scan for vulnerabilities.
- Relate the three techniques useful for validating target vulnerabilities.
- Explain the four-stage methodology of conducting penetration tests.
Deze cursus is enkel beschikbaar in het Engels. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.
Deze cursus is enkel beschikbaar in het Frans. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.

Though technology changes rapidly, the need to assure the confidentiality, integrity, authenticity, and accountability of information does not. Understanding the basics of cryptography is fundamental to keeping your networks, systems, and data secure. In this course, Lisa Bock reviews the historical and present-day uses of encryption, including techniques such as symmetric and asymmetric encryption, algorithms, and hashing. She also reviews message digest and passwords and discusses practical ways to apply cryptography to ensure data security and integrity. By the end of this course, you'll have a solid understanding of what it takes to move and store data securely.
Topics include:
Deze cursus is enkel beschikbaar in het Engels. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.
Deze cursus is enkel beschikbaar in het Frans. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.

Cybersecurity can be daunting because of its technical complexity and the ever-changing threats to individuals and organizations. And more than ever, cybersecurity also is a core business function for organizations of all kinds. Just like other business issues—like finance, legal, or human resources—cybersecurity has its own set of external policies, laws, rules, established practices, and resources for getting help. Getting to know these policies and resources better across your organization—and not just within your IT department—can be hugely beneficial to your company. This course seeks to make key cybersecurity policies and resources clear and understandable—whether you work in IT, in business, or are just interested in how information security fits in with our public policies and laws. Join instructor Gregory Michaelidis to improve your personal or organizational cybersecurity with grounding in the latest regulations, governmental authorities, and resources available.
Topics include:
Deze cursus is enkel beschikbaar in het Engels. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.
Deze cursus is enkel beschikbaar in het Frans. Als dit voor u geen probleem vormt, dien dan gerust uw aanvraag in.
